
Total Endpoint Protection
Secure Every Device. Defeat Every Attack. Traditional antivirus isn't enough. We provide advanced, AI-driven protection (EDR/XDR) for all your endpoints—laptops, mobiles, servers, and even medical IoT—stopping ransomware before it holds your data hostage.
Your Laptops are the New Front Line. Are They Ready?
In a distributed world, your network perimeter has dissolved. Today, every doctor's tablet carrying patient charts and every lawyer's smartphone with client emails is a potential entry point for cybercriminals.
Legacy antivirus cannot stop modern, sophisticated attacks like "fileless malware" or zero-day exploits. Attackers know this. If just one device falls, the entire corporate network follows in minutes. You need protection that thinks faster than the attackers.
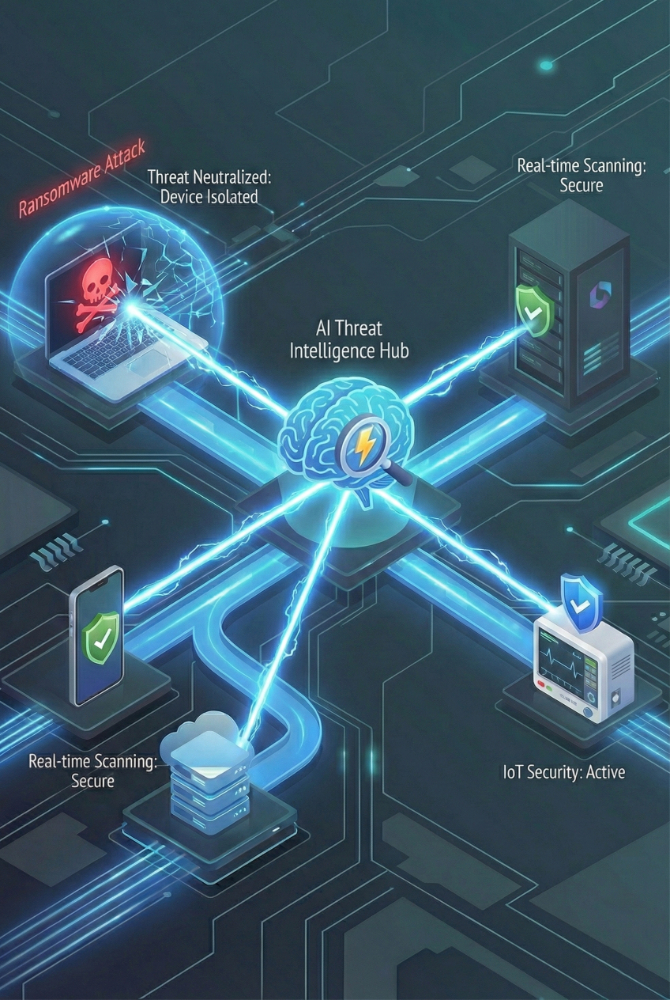
Powered by Next-Gen EDR & XDR Technology.
- AI-Driven Threat Detection (EDR): We don't just scan for known virus signatures. We use behavioral AI to monitor how programs act. If a process suddenly starts encrypting files like ransomware, our system kills it instantly, even if it's a brand-new threat never seen before.
- Mobile Device Management (Intune): Secure the smartphones and tablets your staff use. We enforce PINs, demand encryption, and can remotely wipe corporate data from lost or stolen devices without touching the user's personal photos.
- Server Workload Protection: Your servers hold your most critical data. We apply hardened security policies specifically designed for server environments, protecting your core infrastructure from lateral movement attacks.
- Specialized Device Security (IoT/IoMT): (Crucial for Healthcare): We extend protection to critical medical hardware (IoMT) that cannot run standard antivirus, closing a dangerous security gap in modern hospitals.

Closing the "Device Gap" in UAE Compliance Regulations.
UAE Federal Law No. 2 and DESC standards mandate robust measures to maintain data integrity and confidentiality. An unencrypted laptop left in a taxi isn't just bad luck; it's a reportable data breach incident under Dubai regulations that can lead to severe penalties.
How we solve it: We ensure every single endpoint handling sensitive UAE data—whether it's in the office or at a conference—is encrypted, monitored, and compliant with local security mandates. We provide the audit trails to prove that a lost device was secure.

We Don’t Just "Detect." We "Respond."
An alert at 3 AM is useless if no one is watching. Legal Gridlock provides 24/7 Managed Detection and Response (MDR). Our security team monitors your endpoints around the clock. If a threat is detected on a doctor's laptop, we don't just send an email; we isolate that device remotely from the network immediately, stopping the infection from spreading while we neutralize the threat.
