
Cloud Security Posture Management
Your Cloud is Changing Every Minute. Is Your Security Keeping Up? 99% of cloud security failures are due to misconfiguration. We provide continuous monitoring and automated remediation for your Microsoft Azure and 365 environments to close security gaps before attackers find them.
The "Open Door" You Didn't Know You Left Open.
Moving to the cloud offers speed and scalability, but it introduces a new risk: Complexity. A single engineer clicking the wrong button can accidentally expose thousands of patient records or legal files to the public internet.
This is called "Cloud Drift." Your environment might be secure today, but what about tomorrow? Without continuous scanning, you are flying blind. Legal Gridlock turns the lights on, giving you complete visibility into every server, bucket, and user identity in your cloud.
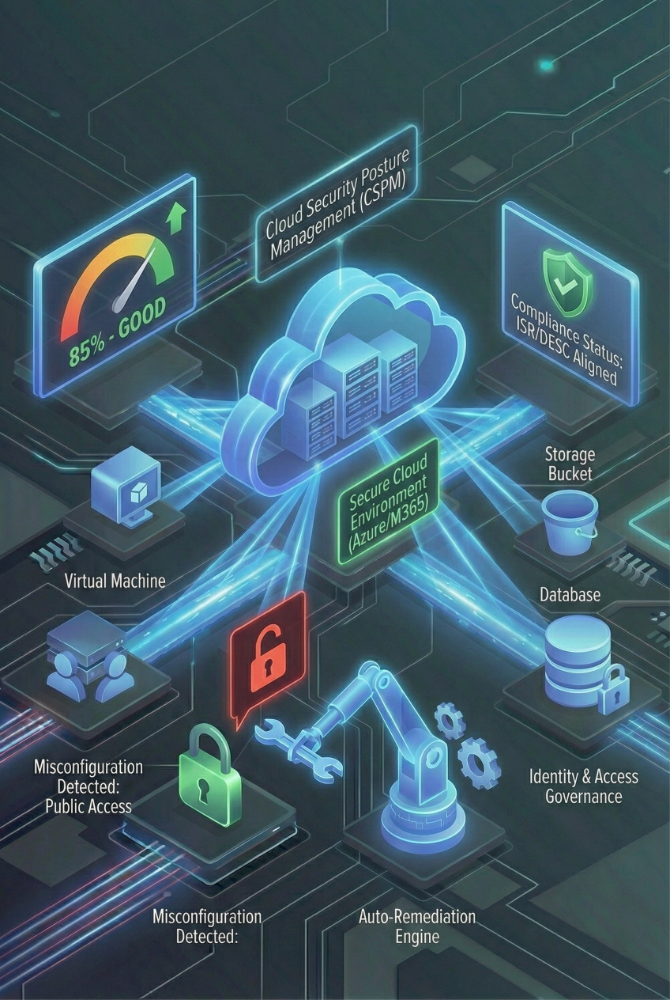
Powered by Microsoft Defender for Cloud.
-
Continuous Configuration Scanning: We don't scan once a year. Our systems monitor your Azure and M365 tenants 24/7. If someone disables Multi-Factor Authentication (MFA) or opens a dangerous firewall port, we know instantly.
-
Secure Score Improvement: We gamify your security. We work to constantly improve your Microsoft "Secure Score," providing you with a quantifiable metric that proves to your board (and auditors) that your posture is getting stronger.
-
Identity & Access Governance: We identify "over-privileged" accounts. Does a junior marketing intern really need admin access to the entire database? We spot these risks and enforce Least Privilege access automatically.
-
Shadow IT Discovery: We find the cloud applications your employees are using without IT's permission, bringing "Shadow IT" into the light and under your control.

Ensuring Your Cloud Meets UAE Data Sovereignty Laws.

